Description
Admin backend story catalog blind SQL injection via post parameters.
Affected Version
DedeCMS <= 5.7.160
POC
- Login to admin backend management.
- Request to
/dede/story_catalog.phpwith GET parameteraction=uprankand POST parametersrank_1=1'+and+sleep(3)+and+'1, this payload will lead to a time-based SQL injection. - Requires
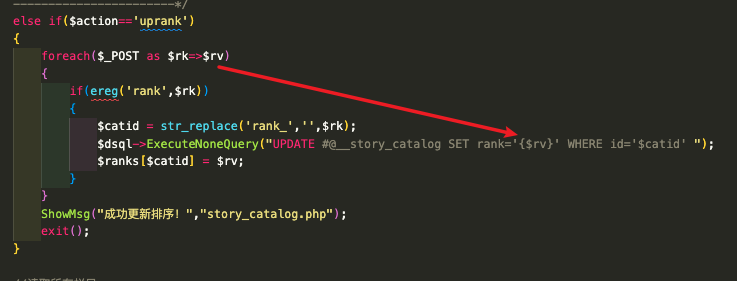
PHP ≤ 5andMySQL ≤ 5.5, and the story component contains at least one record in database. - In the source code of
/dede/story_catalog.php, when the GET parameteractionisuprank, the POST value which the key containsrank_will be directly joined into the update SQL statement, which lead to SQL update injection, finally the joint statement will be passed throughmysqli_query, but this function only return boolean value when the query string is an update statement, that is why this is a blind injection.
Full POC request:
1 | POST /cms/dedecms/dede/story_catalog.php?action=uprank |
Reference
Reported by Srpopty, vulnerability discovered by using Corax.